The Hitler “Ransonware” (Another attempt to steal your money)
Cybercrooks have put together Hitler-themed ransomware that simply deletes files on encrypted PCs.
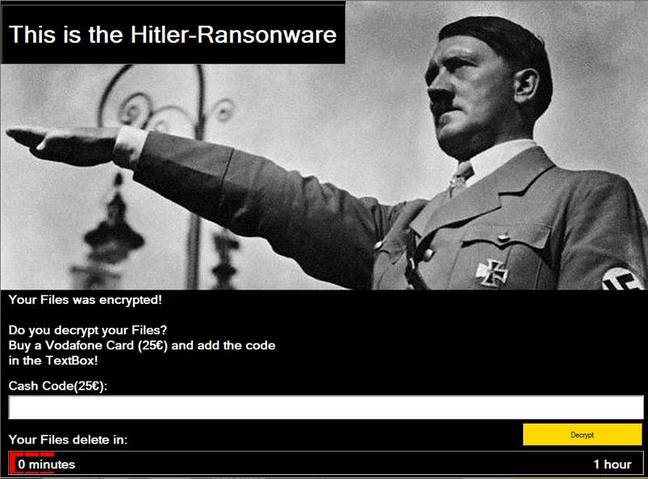
The (apparently prototype) Windows malware displays a lock screen1 featuring the infamous Austrian dictator, together with a demand falsely stating that files have been encrypted.
The ransomware says files can supposedly be recovered by paying 25 euros, in the form of a Vodafone cash card – which is more traceable than BitCoin.
The ransomware appears to be a test variant put together by unskilled coders, as a blog post by IT help site Bleeping Computer explains.
“It does not encrypt any files at all. Instead this malware will remove the extension for all of the files under various directories, display a lock screen, and then show a one hour countdown as shown in the lock screen below.
After that hour it will crash the victim’s computer, and on reboot, delete all of the files under the [use profile] of the victim,” it adds.
German language text found within an embedded batch file associated with the malware states “Das ist ein Test” (“This is a test”)…
Malware that falsely claims to have encrypted files when in reality it has deleted them has been seen before, in the shape of the earlier Ranscam threat – so the Hitler ransomware is no more innovative as a scam than it is as a piece of malicious code.
Thomas Pore, director of IT at security analytics firm Plixer, reckons the half-baked cybercrime threat could still make money.
“It’s interesting that this variant does not actually encrypt the files, possibly for detection avoidance,” Pore said. “However the approach to delete all of the files upon reboot after initiating an OS crash leaves users few alternatives. This is why users will likely continue to pay the ransom…”
Source: “The Register”. Read the complete article here.