Two-Factor Authentication (2FA) vs. Passkeys: Which Security is Best for You?
Many of you are looking to learn more about passkeys and wondering which is better: Passkeys or 2FA.
For years, experts have been telling us to stop relying on passwords alone. The result has been the rise of two major security methods: 2FA and the new kid on the block, Passkeys.
They both protect you, but they work in very different ways. Here is a simple breakdown of the old way versus the new way of logging in.
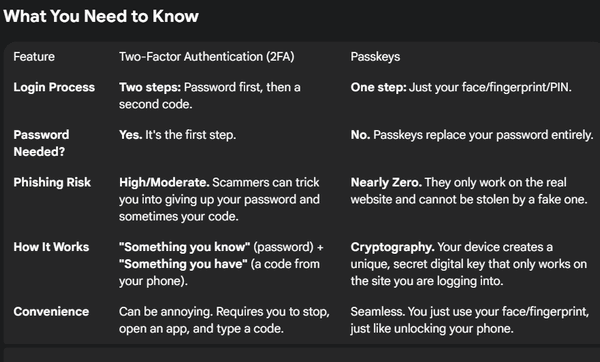
Two-Factor Authentication (2FA)
Think of 2FA as adding a strong lock to a weak door (your password). Even if a hacker steals your password, they are still stopped by the second lock.
How 2FA Works:
You still type your password, but then you need a second factor to prove you are you. This second step is usually:
A text message code (SMS): The weakest, as phone numbers can be “swapped.”
An authenticator app (like Google/Microsoft Authenticator): A code that changes every 30 seconds. This is the gold standard for traditional 2FA.
A physical security key (like a YubiKey): The strongest form of 2FA, but requires buying a little gadget and taking it with you if you’re traveling. If you forget it, you’re out of luck.
The problem with 2FA
You still rely on a password. If a sophisticated hacker sets up a fake website (a phishing scam) and you type in your password and your 2FA code, they can steal both in that second and log into your account before you even know it.
Passkeys
Passkeys are not a second lock; they are a whole new, much stronger door. They completely eliminate the need for a password.
How Passkeys Work:
When you set up a passkey on a website (Google, Apple, Microsoft, etc., are all embracing this technology):
A unique, invisible digital key is created. This key is stored securely on your device (your phone, computer, or a cloud service like your Apple or Google account).
When you go to log in, the website asks your device for that key.
Your device asks you to verify yourself using your fingerprint, face scan, or PIN.
Once confirmed, your device proves it has the key, and you are logged in—no password or code entry required.
The biggest advantage? Passkeys are tied to the specific website they were created for. If a scammer sets up a fake website, your device will refuse to use the passkey, making phishing scams impossible.
Passkeys are significantly better. They offer stronger security and much greater convenience, making it nearly impossible for hackers to steal your login credentials through a phishing attack or data breach.
Use Passkeys Wherever You Can
You should use passkeys whenever you can. If a website or web service offers a passkey option, use it. It is the most secure and easiest way to log in. For sites that don’t yet support passkeys, using 2FA is a must. If you are using 2FA, be sure you’re using an Authenticator App (like Authy or Google Authenticator). Remember that SMS (text message) is still much better than no 2FA at all, but weaker than using an authenticator app.
Popular Authenticator Apps
Many apps are available, but the most widely used ones include:
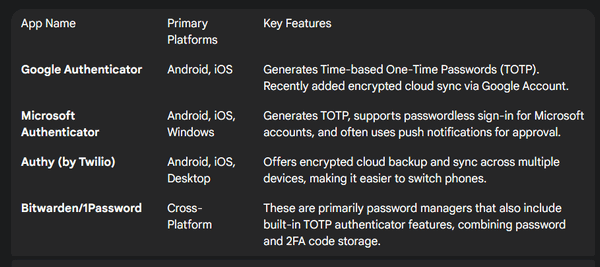
Always download these apps directly from the official app store to ensure you are getting the legitimate version and not a malicious imitation or a legitimate version bundled with malware.
We hope you found this article helpful!


Ok, I’ve not seen this explained enough to quite get the Passkey concept as it relates to a PIN. If it’s stored on your device, how does the website know it’s you? Doesn’t the website need to have that stored somewhere to validate it, just like passwords? I can see where a biometric passkey like a fingerprint or facial recognition are unique. But it seems like anyone can steal your PIN, or couldn’t the PIN be hacked by brute force. Usually PINs are much simpler than passwords.
Explanations I’ve seen (e.g. – https://youtu.be/5eZP_7uZPrU?si=8ervVXplWPMQSBBY) talk about passkeys as not having to be remembered or typed in like a password (true for the biometric type). But a PIN is definitely remembered and typed in. Can you explain further the diff between a PIN and password?
Thanks
You’re not alone Bruce–I still don’t get it quite yet either. Passkeys are usually 4 letters, so it seems likely that others will also be using the same passkey as me. Also…Can I use the same passkey everywhere? Hopefully someone can expand on this.
The PIN you type in is the PIN you use to log into your computer, tablet, or smartphone. If you use a fingerprint or face scan to unlock you phone or tablet you would you would use your facr or fingerprint to unlock your Passkey. If you Windows computer does not have biometrics then you use the PIN that unlocks your computer to unlock your passkeys.
Another question what happens to those sites and passkeys that are fingerprints and face recognition if you die people will not be able to get into your computer, phone, Ipad and such. My grandson had devices and when he died we could not get into them. So I just don’t know about that.
The relative must be set up as a Trusted Contact using Google’s Inactive Account Manager. If the account remains inactive for a set period, the trusted contact is notified and given access to the data the deceased chose to share (which can include passwords/passkeys).
They can alos use third-Party Password Managers. Most paid password managers (like LastPass, 1Password, Keeper, Bitwarden, etc.) have an Emergency Access or Digital Inheritance feature. The deceased would have designated a trusted relative as an emergency contact. That person can then request access, which is usually granted after a set waiting period (in case the owner is just incapacitated, not deceased) or upon submission of documentation.
Those are two ways that passkeys can be used to access accounts of someone who has passed away.
I tried them and no, I donèt like them. To me, it seems as if the passkeys are just glorified passwords with just as much memory needed for them. I could be wrong and am just fed up with the whole lot of junk trying to protect us. Oh for the good old days when computers first came in!!!
Passkeys require no more computer memory than passwords and even less than passwords plus 2FA. If every one used passkeys there would be no more phishing and data breaches would be less devastatting.
If I set a passkey using my fingerprint on my android phone, I will still need to use a 4-digit code on my laptop (which does not have a pad for my fingerprint). How will the site I am attempting to enter will know that it should let me in no matter which device I’m using?
Also, someone gave me a security key – it looks like a flash drive with a USB C and some sort of button with the photo of a key. I’d have to download an app to my phone and always use this physical “thing” on my phone or laptop to access my passkey. It seems cumbersome. Is it a better solution than using my bitwarden which I’ve synced between my phone & laptop?